Before You Begin
Before we dive into some code we think it would be a good idea to explain:
- What RBAC is
- How leveraging RBAC can help you manage and improve your application's access control and security
- How Authentication and Authorization differ
- What PHP-RBAC has to offer you and your project
Why use RBAC?
Role Based Access Control is the standard means of authorization (access control). The other approach is ACLs, where a table defines who can do what. ACLs are only good for very small systems, because of the following reasons:
 Big systems have lots of permissions
Big systems have lots of permissions People move in organizations, and all their permissions should be changed when they do
People move in organizations, and all their permissions should be changed when they do Maintenance (adding, changing, removing) of 100,000 permissions requires a handful of staff
Maintenance (adding, changing, removing) of 100,000 permissions requires a handful of staff Maintenance of the permissions assigned to each user, requires more staff than above!
Maintenance of the permissions assigned to each user, requires more staff than above! One wrong user-permissions and you have a serious breach in your security, so no room for error
One wrong user-permissions and you have a serious breach in your security, so no room for error
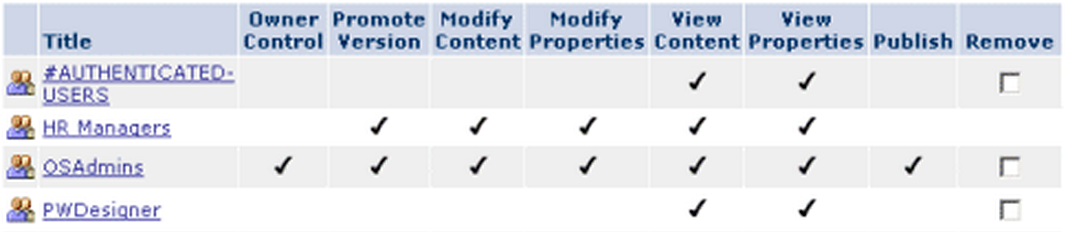
Example of an ACL
Usage of ACLs has led to broken authorization and access control all over applications, and authorization is limited only to critical operations to keep the number of permissions low.
But RBAC is here to save the day.
What is RBAC?
RBAC separates the concepts of Users, Roles and Permissions. Roles are defined in a system, then Permissions defined separately. Then the security administrator decides what role should be permitted to do what action, by assigning that role to the permission. Finally users are assigned to roles. The system does the rest.
 Still lots of permits in the system are the problem
Still lots of permits in the system are the problem People move, and only their roles need to be changed
People move, and only their roles need to be changed Maintenance of permits is still an issue
Maintenance of permits is still an issue Maintenance of permits assigned to each role is easy, it doesn't change much logically.
Maintenance of permits assigned to each role is easy, it doesn't change much logically. Role-Permission assignments can be double checked so that no wrong permit is given to any role
Role-Permission assignments can be double checked so that no wrong permit is given to any role
That was NIST Level 1 standard RBAC above, and it still had issues. NIST Level 2 RBAC requires Roles and/or Permissions to be hierarchical, so that management of them can easily be handled in hierarchies. The figure below demonstrates a system in hierarchical RBAC:
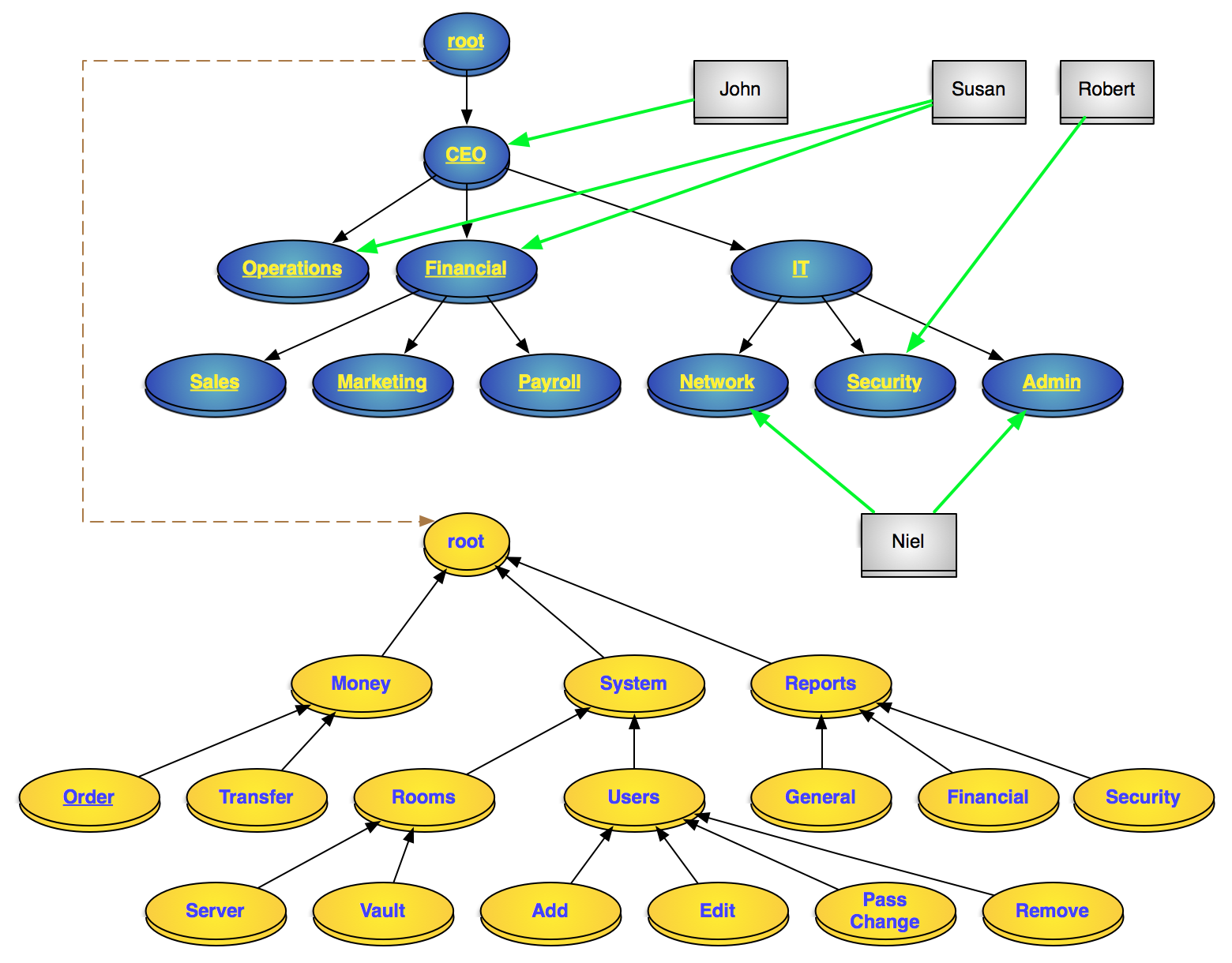
A hierarchical RBAC model of a system
Blue: roles, Gray: users, Yellow: permissions
Authorization vs Authentication
Authorization and Authentication are two different beasts!
A reliable Access Control System should include at least these four pieces:
- Authentication
- Authorization
- Access Approval
- Audit (audit logs/trails)
In this discussion we will focus on the two pieces that often cause confusion to those new to Access Control Systems:
- Authentication and Authorization
Authentication
Authentication... is the act of confirming the truth of an attribute of a datum or entity. This might involve confirming the identity of a person or software program, tracing the origins of an artifact, or ensuring that a product is what its packaging and labeling claims to be. Authentication often involves verifying the validity of at least one form of identification.
Authentication verifies and confirms that something really is what it says it is.
In most cases you will be Authenticating the identity of a User, so lets use a User Entity as a basic example of how an Authentication System works:
- The User is provided with a Form which prompts the User for their Username and Password
-
The Authentication System will then attempt to validate the provided credentials
- If the provided credentials are incorrect the Authorization System, depending on the defined Authorization Policies, may allow the User to attempt to provide the proper credentials again
- If the provided credentials are valid the Authentication System will then perform the neccessary "Magic" to 'Log In' the User
- From this point on it is up to the Authentication System to track/monitor the User and make sure the User continues to be validly Authenticated.
Authorization
Authorization or authorisation is the function of specifying access rights to resources, which is related to information security and computer security in general and to access control in particular. More formally, "to authorize" is to define access policy.
An Authorization System is used to manage Access Rights, and to keep track of what Access Rights an Entity has.
This is the sole purpose of PHP-RBAC
PHP-RBAC makes it easy for you to define Access Rights by creating hierarchies of Permissions and Roles, assigning Permissions to Roles, and then assigning Roles to Users/Entities.
PHP-RBAC then allows you to easily check if a User has the proper Access Rights that are needed to access a specific Resource (Does the User have Role_x or Permission_y assigned to them?).
When a User navigates to a restricted Resource your application will ask PHP-RBAC if this User has the proper Access Rights to access this Resource:
- If the User has the proper Access Rights (Role/Permission) PHP-RBAC will return 'true'
- If the User does not have the proper Access Rights (Role/Permission) then PHP-RBAC will return 'false'
Keep in mind
- An Authorization System allows you to easily create and manage Access Rights
- An Authorization System lets you know if an Entity has the proper Access Rights to a Resource when asked
- An Authorization System does not define application behavior (grant/deny) that is triggered when an Entity does or does not meet the requirements of a Resource's Access Rights
- It is up to your application to Authenticate your Users
- It is up to your application to grant/deny access to Resources based on what PHP-RBAC returns regarding the Users Access Rights
What does PHP-RBAC offer?
NIST Level 2 Standard Hierarchical Role Based Access Control
PHP-RBAC is the de-facto authorization library for PHP because it provides developers with a NIST Level 2 RBAC compliant Access Control System right at your finger tips.
NIST Level 2 RBAC compliance means:
- A secure, flexible, reliable, and standardized RBAC system that will conform to your application's custom Access Control Policy needs without the headache.
To learn more about NIST Role Based Access Control standards please visit the NIST website:
An extremely fast implementation
PHP-RBAC is designed to be used in applications with a high load of Access Right checks, and has been optimized for blazingly fast queries.
Ease of use
PHP-RBAC is not only extremely fast, but it is extremely easy to use!
Because of the thought and care that went into designing our API, PHP-RBAC's simple and elegant API hides the power and complexity of it's core, allowing you to get your work done as fast and painless as possible.
A sense of security
While using PHP-RBAC you can feel safe and secure that you are using a powerful, professional tool developed by knowledgeable developers that are just as aware and concerned about application security as you are, and who work hard to release only the highest quality profession tools possible.
Even though we provide these tools for other developers to leverage, we use these tools in our own applications. Our goals towards quality and usefulness isn't just aimed at you. We want to make our lives easier too!
Continue...
You are now ready for the next step: Getting Started